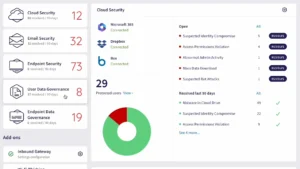
There’s probably no place on earth where we’re more vulnerable than a doctor’s office or hospital. You not only share sensitive information about your mental and physical condition but also your family history, your social security numbers, your treatment plans, medication, email, credit card number, insurance information, and more.
While hospitals and insurers are trying to step up their cybersecurity game, your data may already be in the wrong hands. According to the UnitedHealth Group, “a substantial proportion of people in America” may have been affected by a breach against its health-tech subsidiary, Change Healthcare, back in February.
About the Change Healthcare Cyber Attack
UnitedHealth released a statement on April 22, 2024, informing the public that a ransomware attack against Change Healthcare resulted in a significant theft of private healthcare data.
Change Healthcare is responsible for processing the insurance and billing for several hundred thousand medical facilities, including medical practices, pharmacies, and hospitals. This means that it has access to vast quantities of healthcare data related to nearly half of all Americans.
The company stated that it will take several months before the extent of the theft can be determined, which means affected individuals will likely only be notified much further down the line.
While there hasn’t been any evidence that charts or full medical histories have been extrapolated, hackers have already started publishing portions of stolen data on the dark web in an effort to demand more ransom money from UnitedHealth.
A company spokesperson for UnitedHealth confirmed that an initial ransom was paid for the attacks. UnitedHealth hasn’t confirmed the amount paid, but it’s reportedly as high as $22 million.
Who Carried Out the Attack?
There’s some confusion surrounding the perpetrators of the Change Healthcare cyber attack. ALPHV/BlackCat is widely believed to be the main perpetrator behind the attack. Change Healthcare itself confirmed they were dealing with ALPHV/BlackCat during the incident and that they made a payment to the group in March.
However, another group, RansomHub, emerged, claiming to possess stolen data from the attack. They demanded a ransom payment and threatened to release the stolen information.
Some reports suggest RansomHub might be linked to ALPHV/BlackCat and are possibly a splinter group or using the opportunity for further extortion. Others have speculated that RansomHub carried out the data theft on behalf of ALPHV, who took the payment and cheated RansomHub out of their portion of the ransom.
When RansomHub published the stolen data, they posted a statement that said, “We have the data and not ALPHV.” Some of the files published included billing files and insurance records, as well as contracts and agreements between Change Healthcare and its partners. RansomHub threatened to sell the data to the highest bidder if the money wasn’t paid.
UnitedHealth acknowledged that the files were published but said that it was “not an official breach notification” and did not claim ownership of the documents published.
How Was the Attack Carried Out?
According to the Wall Street Journal, hackers broke into Change Healthcare’s network on February 21 using stolen credentials to access a system that grants remote access to its network. Multifactor authentication protocols (MFA) that usually protect systems like these against breaches had not been enabled for this application.
The attackers were able to remain inside the network for a week before deploying ransomware, which gave them ample time to steal data.
The attack caused widespread outages at hospitals and pharmacies that lasted several weeks as medical professionals were unable to verify patient benefits or process prior authorizations. This led to tremendous financial pressure and backlogs, with UnitedHealth suffering losses of $870 million.
Who Has Been Affected?
Change processes 15 billion transactions per year, touching one in every three medical records. If this data has been sold, it could have devastating consequences for nearly half of the American population.
There was a ripple effect across the healthcare industry, too: more than a hundred of Change’s systems were shut down, and many smaller providers were unable to take in revenue as a result. This will lead to additional financial consequences for many small businesses.
Another consequence of the attack is increased scrutiny by lawmakers. Many are concerned about the cyber risks that a dominant healthcare company introduces to the US. The US Department of Health and Human Services is also launching its own investigation into the incident.
What Does This Mean For Me?
You may have already been affected by outages and a delay in receiving medication or scheduling surgery as a direct result of this breach. However, stolen data is of even bigger concern.
If you have been impacted by the breach, it will take several weeks or months before you will be notified. Depending on the information stolen (if any), risks may include:
- Names, dates of birth, addresses, Social Security numbers, medical history, diagnoses, treatment plans, medications, and possibly insurance information could already be on the dark web.
- Hackers could use stolen data to impersonate you and get medical treatment or prescriptions in your name, potentially leading to incorrect treatment or difficulty getting the care you need.
- Medical identity theft could lead to fraudulent charges on your insurance or bills for services you never received.
Take control. Monitor your health insurance statements and credit reports closely. Look out for any suspicious activity, like charges for services you never received or new accounts opened in your name.
If you suspect someone has stolen your credit information, place a fraud alert on your credit so that they can’t open new accounts in your name. If you suspect identity theft, report it to the Federal Trade Commission (FTC) at identitytheft.gov.
It’s also a good idea to change your passwords, particularly for any accounts linked to your health insurance or medical care. Use strong, unique passwords for each account and enable two-factor authentication (2FA) where available.
Most of all, review your privacy settings and permissions with your insurance provider. Understanding how your information is collected and stored empowers you to make good decisions about your security.
Remember too, while this was a gigantic healthcare breach, it’s just one of many this year alone. Right now, we’re just learning of a Kaiser Permanente data leak that has impacted millions of its members. And we’re not even six months into the year.
If you’re a healthcare company interested in stronger prevention for your data, see how Coro can help.